Manual Process
- Navigate to IAM -> Roles -> Create role
- Select “Another AWS account” as a type of trusted entity.
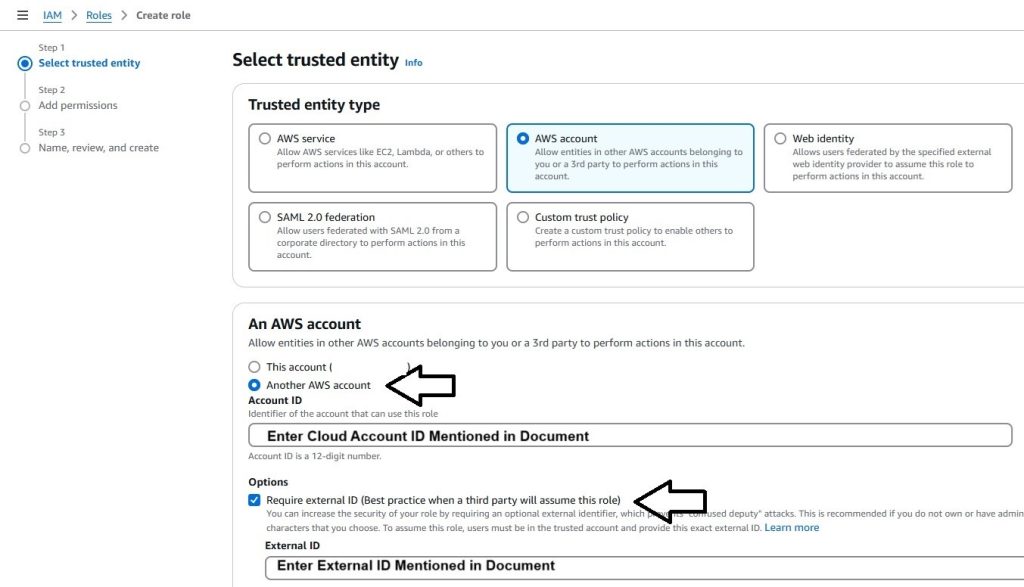
- Enter Cloudlytics AWS Account ID: 891776519288
- Check “Require external ID” and enter External ID: Please Use External ID as shown on Cloudlytics Console.
- Do not check the “Require MFA” option.
- Click Next: Permissions
- Search and select the “Read Only Access” policy
- Add tags (optional)
- Review all the details
- Enter role name and role description(optional) and click on create role .
- Search for the newly created role and click on it .
- Copy the Role ARN value and paste it below.
Automated Process
- Click the launch cloudformation stack .
- If you want to use WAR feature on Cloudlytics, Use cloudFormation template , or launch cloudformation stack here.
- Check “I acknowledge that AWS CloudFormation might create IAM resources with custom names.” and click Create
- Once successfully Created, copy roleARN from the output section and paste it below.
Note: If the stack is not shown you might need to click refresh button





